Cybersecurity Threats & Attacks
Explore the world of cybersecurity threats and learn about different types of attacks, their prevention, and protection strategies.
📚 Common Cyber Threats
🦠 Malware Types
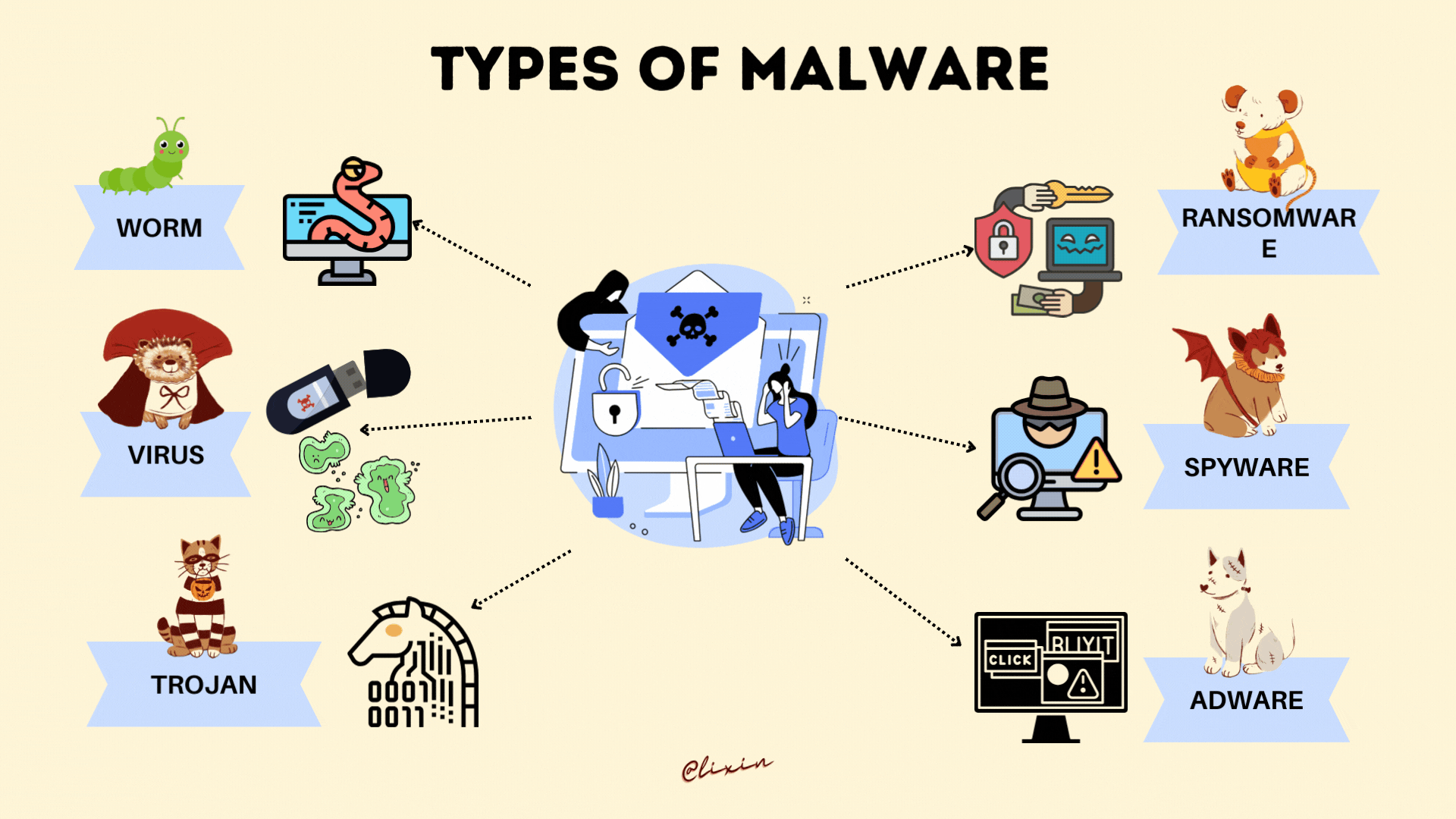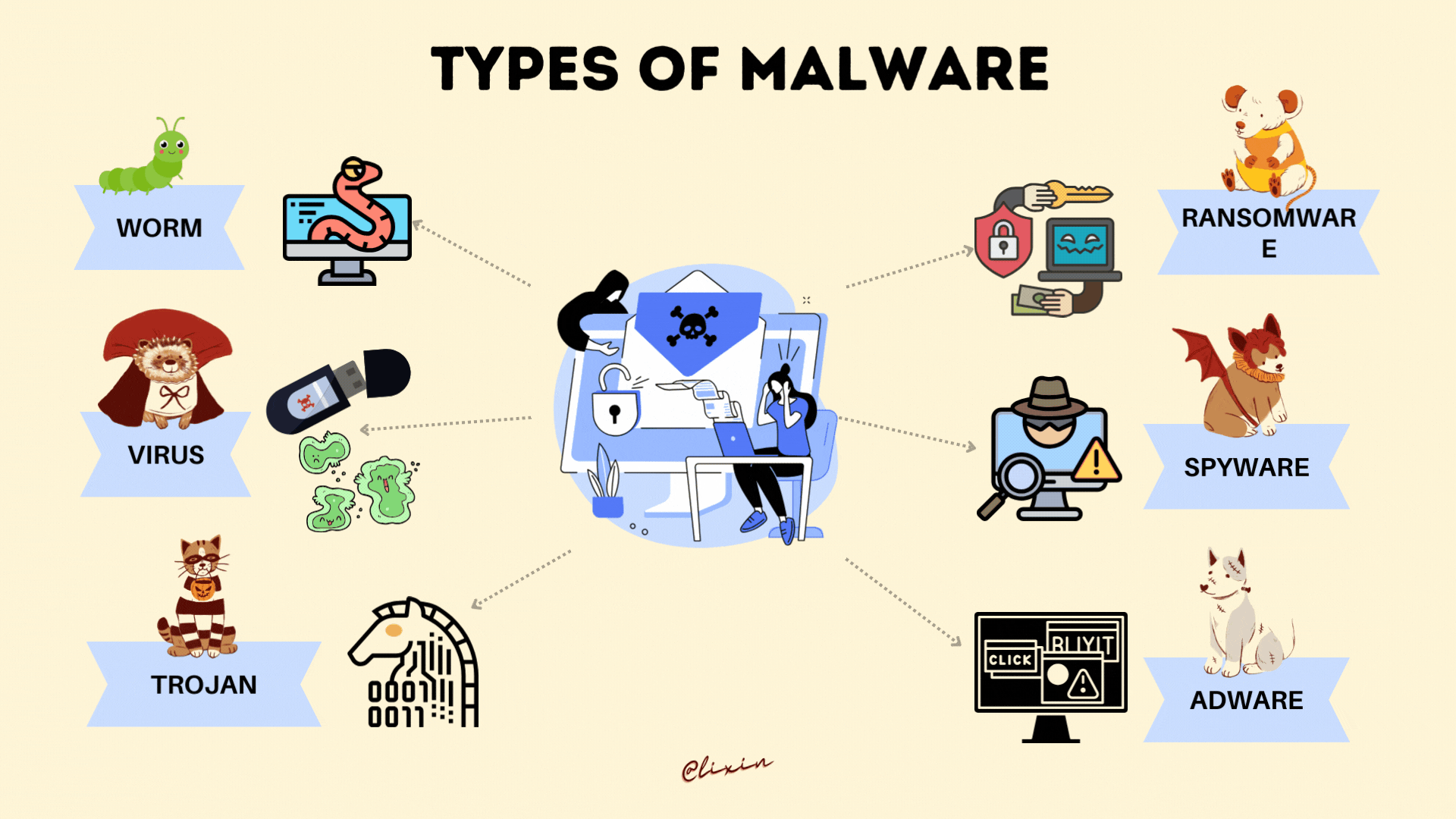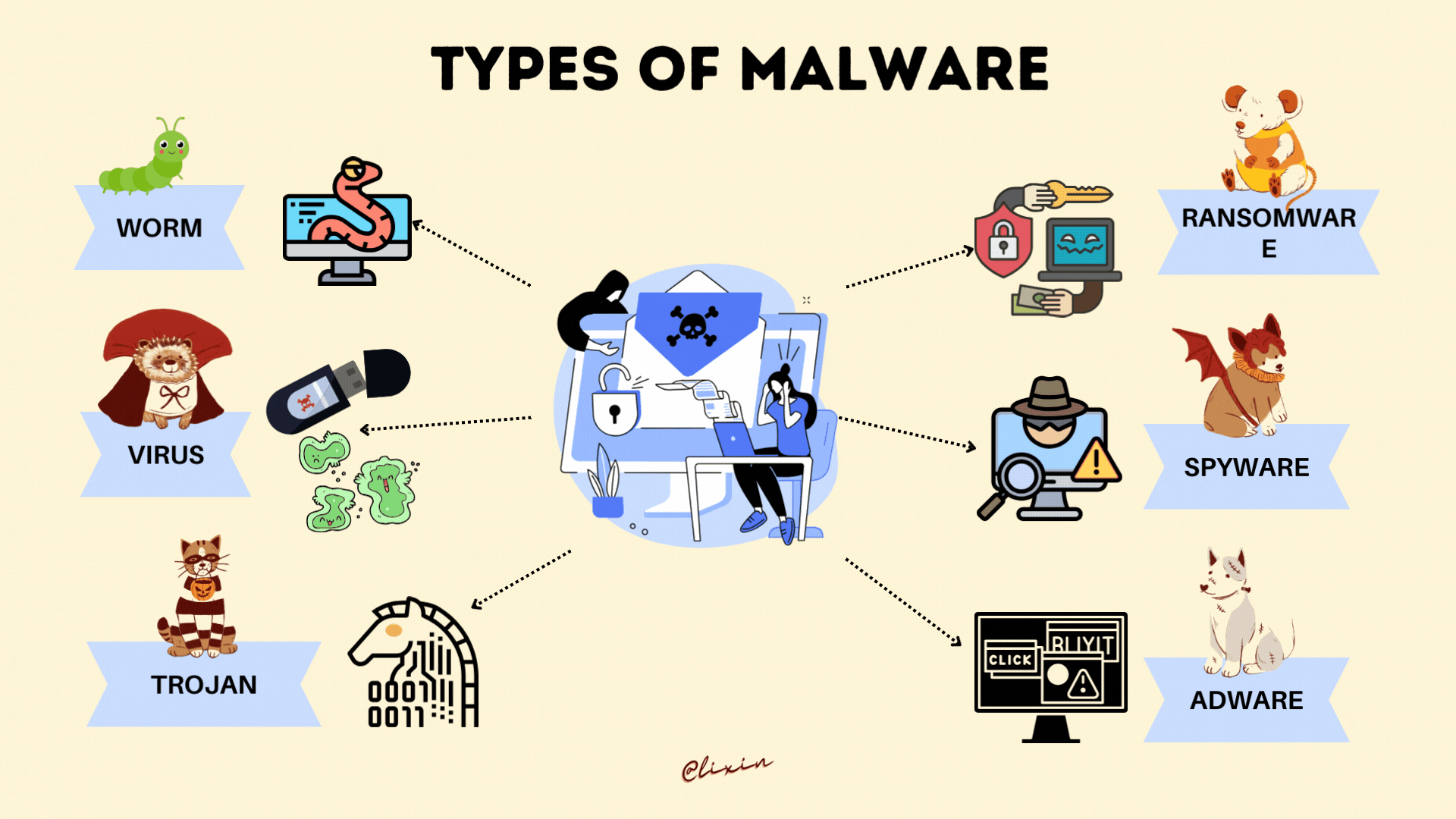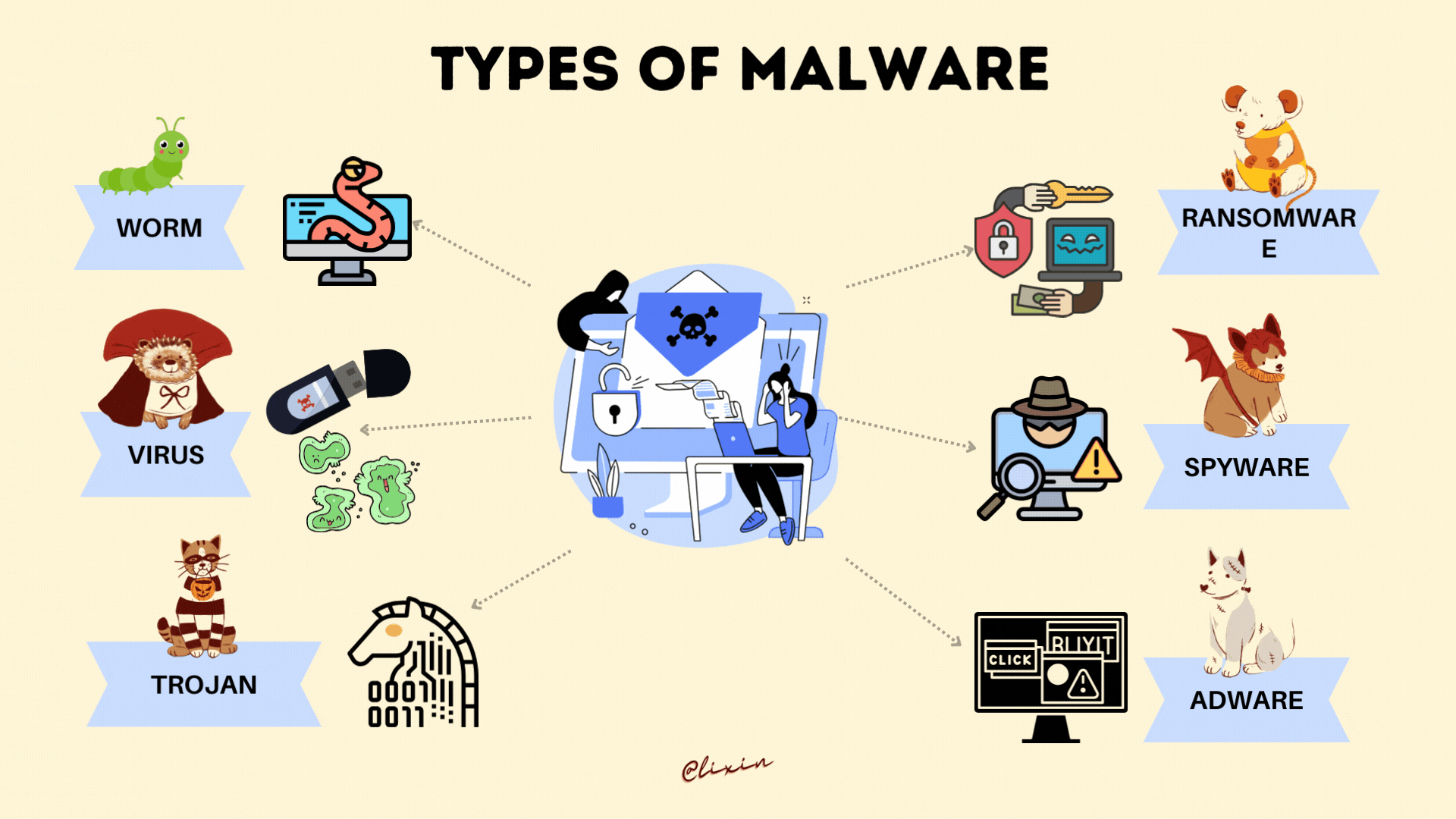
Common Malware
- 🔴 Ransomware - Data Encryption Attacks
- 🔴 Trojans - Deceptive Malware
- 🔴 Spyware - Information Stealing
Advanced Threats
- 🟠 Rootkits - System Level Access
- 🟠 Botnets - Network of Infected Devices
- 🟠 Cryptojacking - Crypto Mining Malware
🎯 Attack Vectors
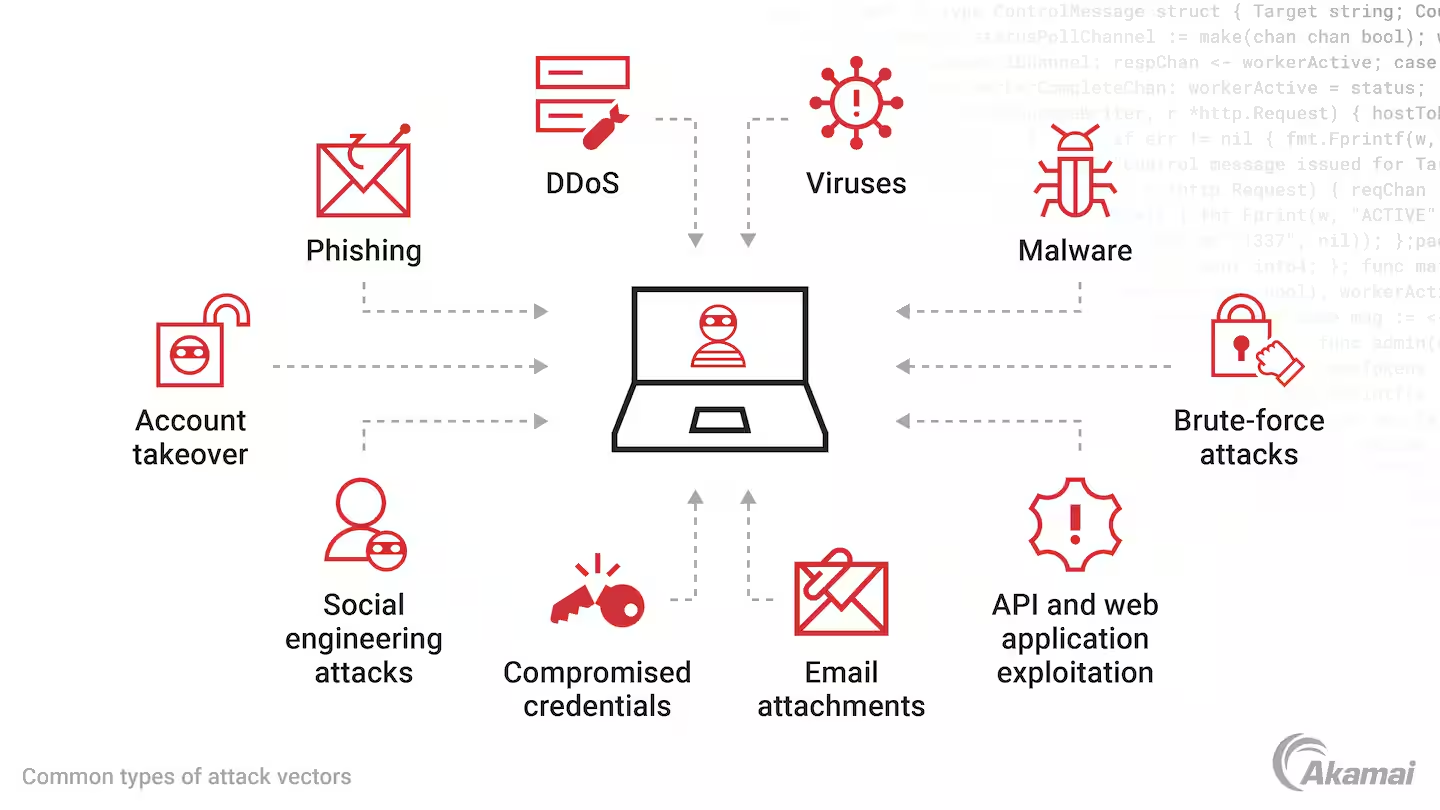
Common Attacks
- 📘 Phishing - Social Engineering
- 📘 SQL Injection - Database Attacks
- 📘 XSS - Web Application Attacks
Advanced Attacks
- 📗 MITM - Network Interception
- 📗 DDoS - Service Disruption
- 📗 Zero-Day - Unknown Vulnerabilities
🛡️ Protection Tools
Security Software
- 🔧 Malwarebytes - Anti-Malware
- 🔧 Wireshark - Network Analysis
- 🔧 Nmap - Network Scanner
Security Practices
- 🔍 Cyber Hygiene - Best Practices
- 🔍 Ransomware Prevention - Protection Guide
- 🔍 Security Awareness - Training Resources
🔒 Network Security

Network Threats
- 🔐 Ransomware - Network Encryption
- 🔐 APTs - Advanced Persistent Threats
- 🔐 Network Malware - System Infections
Protection Measures
📚 Security Certifications
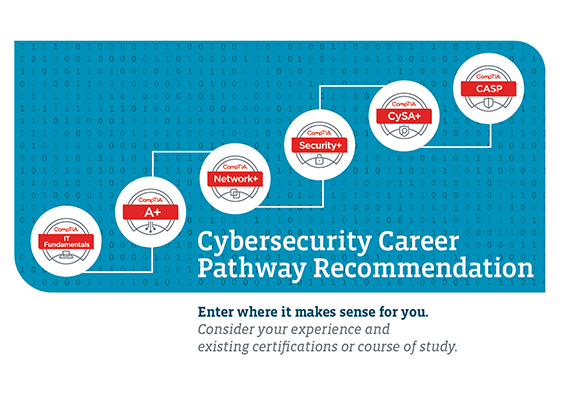
Entry Level
- 📜 Security+ - CompTIA
- 📜 Certified in Cybersecurity - (ISC)²
- 📜 CEH - EC-Council
Advanced Level
🛡️ Practice Labs

Learning Platforms
- 🎯 TryHackMe - Interactive Learning
- 🎯 HackTheBox - Penetration Testing
- 🎯 VulnHub - Vulnerable Machines
Practice Resources
- 🏆 CTF Time - Capture The Flag Events
- 🏆 CyberDefenders - Blue Team Labs
- 🏆 Root-Me - Security Challenges